
How Public & Private Keys protect data
Most people don’t fully understand the concepts of how public and private keys work. We thought it essential to examine what these keys are, what they aren’t, and how they work. This blog presents a comprehensive summary of public and private key pairs rather than an architectural summary of Evol Coin or Evol Network.
How public and private key encryption works
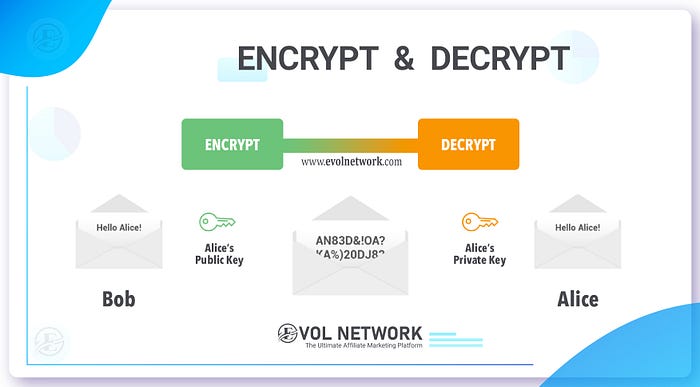
Also known as Asymmetric Cryptography, Public and Private keys make up the foundation of public-key cryptography. In this type of cryptography, each public key matches its private key. Data security needs both jointly to encrypt & decrypt messages to complete the process. The sender encodes a message with a person’s public key. The receiver can only decode it using the matching private key.
For example, John wishes to send an encrypted file to Jane. So, John takes Jane’s public key to encrypt his file to her. When Jane gets the file, she decrypts the file using the private key known only to her.
Though attackers may attempt to hack the server to read the file, they will be unable to as they need the private key. Only Jane is the one with the private key and will be able to decrypt the file. Likewise, when Jane needs to send a file to John, she repeats the process. She will be encrypting her file using John’s public key.
The difference between public and private keys
Public keys are like the address of any business on the Internet, which is readily available publicly. Everyone can look it up and share it with anybody. Public keys, in the case of asymmetric encryption, can be given to everybody in the system. Once the sender has the public key, they can use it to encrypt messages.
Every public key has a corresponding private key. A private key is like the key to the front door of a business. Only the business owner has access to it.
It illustrates one of the significant differences between the two types of keys. The private key makes sure only the owner can use the front door. When sending encrypted messages, the sender can use the private key to decrypt.
Both these keys together ensure the security of the exchanged data. When the sender encrypts a message with the public key, the receiver can’t decrypt it without having its corresponding private key.
Generating public and private keys
Both the public and private keys are not real keys. They are just large prime numbers that are mathematically related to one another.
The receiver can use only the related private key to decrypt whatever is encrypted by the public key. Nobody can figure out the private key on knowing the public key. People can freely share the public key due to this reason. But, only a single person should know about the private key.
There are many popular mathematical algorithms used to create public and private keys. Some of these algorithms include:
Rivest-Shamir-Adelman (RSA) is the oldest public-private key cryptography system. It is often utilised for symmetric-key cryptography to transmit shared keys.
Digital Signature Standard (DSS) is a Federal Information Processing Standard. It specifies the algorithms used to create digital signatures used by NIST.
Elliptic curve cryptography (ECC) relies on elliptic curves to generate keys. Frequently, it is used for digital signatures and key agreements.
Public-private key encryption
Digital signatures
A digital signature assures the receiver that the person sending the message is who they are claiming to be. Public and private keys together form the digital signature.
Typically, the sender uses the recipient’s public key to encrypt the data. Then, the recipient applies the private key for the decryption of the data. Though, there’s no way to authenticate the source using the scheme of digital signatures. Paul can get hold of Jane’s public key and pretend that John is sending a message to Jane.
To create a digital signature, John will digitally sign his email to Jane using his private key. When Jane gets the message from John, she will verify the digital signature. Thus, she will quickly verify that it came from John by using his public key. As the digital signature uses John’s private key, John can be the only person who would be able to create the signature.
Diffie-Helman key exchange
The Diffie Hellman key exchange shows how it is possible to exchange cryptographic keys over a public channel securely.
Earlier, to enable secure encrypted communication, people first exchanged keys using a secure means. For example, using paper key lists transported by a trusted courier. Using The Diffie–Hellman key exchange method lets two parties without prior knowledge of each other share the secret key through an insecure channel.
Business benefits of public-private key encryption
The receiver gets assured that the data is what the sender says it is, using public and private keys for encryption and decryption. The recipient is confident about the authenticity, integrity and confidentiality of the data.
Confidentiality — The receiver will decrypt the message secured with the public key only using the private key. It makes sure that only the intended recipient can only see the contents of the message.
Integrity — As a part of the decryption process, the message received should be the same as the original message. It is to make sure that no one could have changed the message in between.
Authenticity — Jane’s private key also signs every message sent by Jane to John. The only way to decrypt Jane’s private key is with her public key, which John can access. Jane ensures the authenticity of the message by signing it using her private key. It proves that it did come from her.
Public and private key pairs lay the foundation for robust data security and encryption. At Evol Network, we take the security of our customers’ data very seriously. Visit www.evolnetwork.com to learn more about Evol Coin.
- Twitter: twitter.com/evolnetwork
- Instagram: www.instagram.com/evolnetwork/
- Facebook: www.facebook.com/evolnetworks/
- Telegram: t.me/evolnetworkofficial
- LinkedIn: www.linkedin.com/company/evol...
- Reddit: www.reddit.com/r/EvolNetwok/
- Medium: medium.com/@evolnetwork
- Bitcointalk: bitcointalk.org/index.php?act…
- Pinterest: in.pinterest.com/evolnetwork/

